How to identify and analyze the outdated TLS protocol version?
Without the proper website security in place, hackers can quickly access your website, which can have devastating effects on website visitors. Transport Layer Security, or TLS, is a cryptographic protocol that ensures the security of communications between any two devices on a network, the authenticity of transmitted data, and user data privacy. However, the level of security your website actually has depends on the TLS version you use.
Continue reading to learn more about outdated TLS protocol versions and what you can do about them.
Risk of using an outdated TLS version
It is recommended that you have a minimum TLS v1.2 or higher version if you operate an online business or your site handles sensitive information like financial and banking details. Using older versions of TLS would require more work to be done in order to preserve the libraries, which would drive up the cost of product maintenance.
Outdated TLS protocols use cipher suites that are not supported or recommended. Some risks that could occur are:
- Using outdated versions of TLS would compel enterprises to use insecure, outdated cipher suites and prevent them from using more recent, recommended cipher suites.
- Due to the fact that they use SHA-1 hash to verify the authenticity of messages during communication, TLS versions 1.0 and 1.1 are susceptible to downgrade attacks. Indeed the authentication of handshakes depends on SHA-1, which makes it much simpler for an adversary to impersonate a server to carry out a MITM attack. TLS versions 1.1 and lower do not have the opportunity to use more secure hashing methods, although more recent versions of this protocol do.
- The expense of maintaining security, patching vulnerabilities, supporting libraries, and expanding the attack surface are all raised when older protocols are supported.
Ways to identify and analyze an outdated TLS protocol version
Since various manifestations of outdated TLS setups might be seen in traffic, the following identification approach is suggested:
- The first step is to discover the TLS version the client is using and the servers that are negotiating an insecure protocol. No additional traffic analysis is necessary if a client or a server negotiates SSL 2.0, SSL 3.0, or an older TLS version. Instead, remedial procedures should be implemented.
- Next, for TLS 1.2 connections, organizations should locate and update any out-of-date devices or cipher suites. Find clients only giving insecure TLS cypher suites and servers negotiating insecure cipher suites, and then alter their configurations to be compliant.
- Last but not least, businesses should discover and fix devices employing insecure key exchange techniques during sessions utilizing TLS 1.2 or 1.3 and cypher suites.
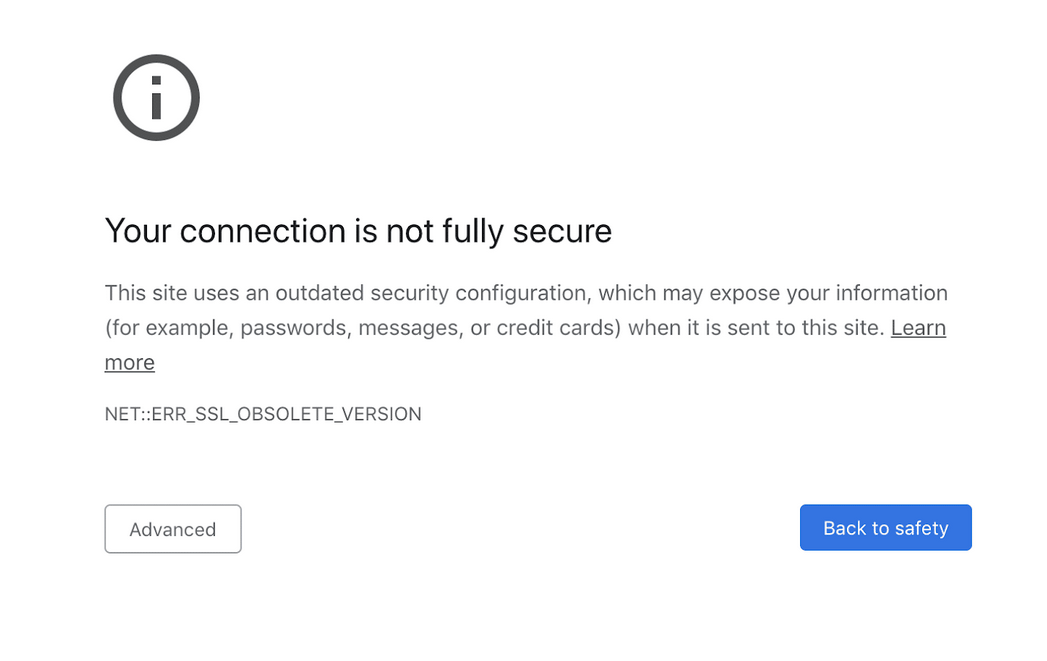
Final word on outdated TLS protocols
The use of HTTPS, which TLS protects, is now an industry standard for websites. Encryption via TLS can assist in the protection of web applications against data breaches and other forms of attack. But the benefit is limited if the TLS protocols are outdated. That’s why it’s important to always maintain your TLS protocols and make updates when a new version is available.
If you’re looking for SEO project management software to better manage your workflow, clients, and business – evisio.co is your solution. Try evisio.co for free here!
